 "TheRealBicycleBuck" (therealbicyclebuck)
"TheRealBicycleBuck" (therealbicyclebuck)
07/17/2020 at 14:37 • Filed to: None
 3
3
 17
17
 "TheRealBicycleBuck" (therealbicyclebuck)
"TheRealBicycleBuck" (therealbicyclebuck)
07/17/2020 at 14:37 • Filed to: None |  3 3
|  17 17 |
It looks like our IT department is testing our employees again. They had an outside company send an “invoice reminder” with a link.
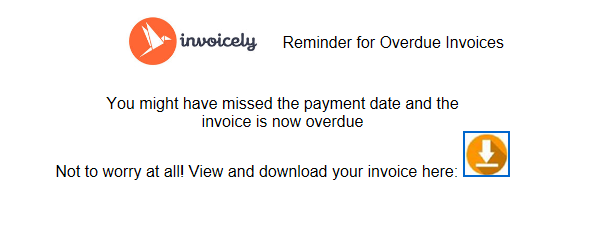
Yeah, right. Nobody should be sending me any invoices and I’m certainly not late on one. I did a little digging and it led me here:
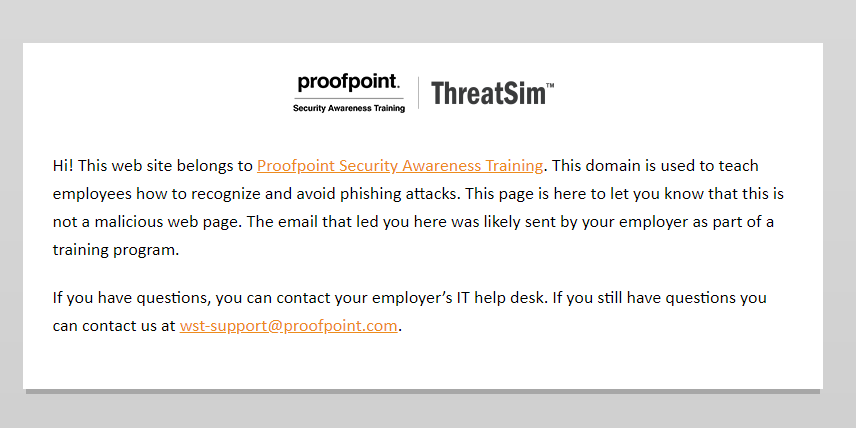
Sorry, IT guys. You’ll have to try harder next time.
 Highlander-Datsuns are Forever
> TheRealBicycleBuck
Highlander-Datsuns are Forever
> TheRealBicycleBuck
07/17/2020 at 14:45 |
|
TBH that’s kind of shitty. Maybe do a better job of educating your workforce on how to internet safely.
 TheRealBicycleBuck
> Highlander-Datsuns are Forever
TheRealBicycleBuck
> Highlander-Datsuns are Forever
07/17/2020 at 14:48 |
|
The problem is that they DO train people on how to internet safely. But people don’t think and click on links and end up in the IT timeout corner for additional training. We’ve had a couple of company-wide virus outbreaks because of people clicking on bogus links.
 For Sweden
> TheRealBicycleBuck
For Sweden
> TheRealBicycleBuck
07/17/2020 at 14:49 |
|
I tried the same thing earlier this week using this message. It went well.
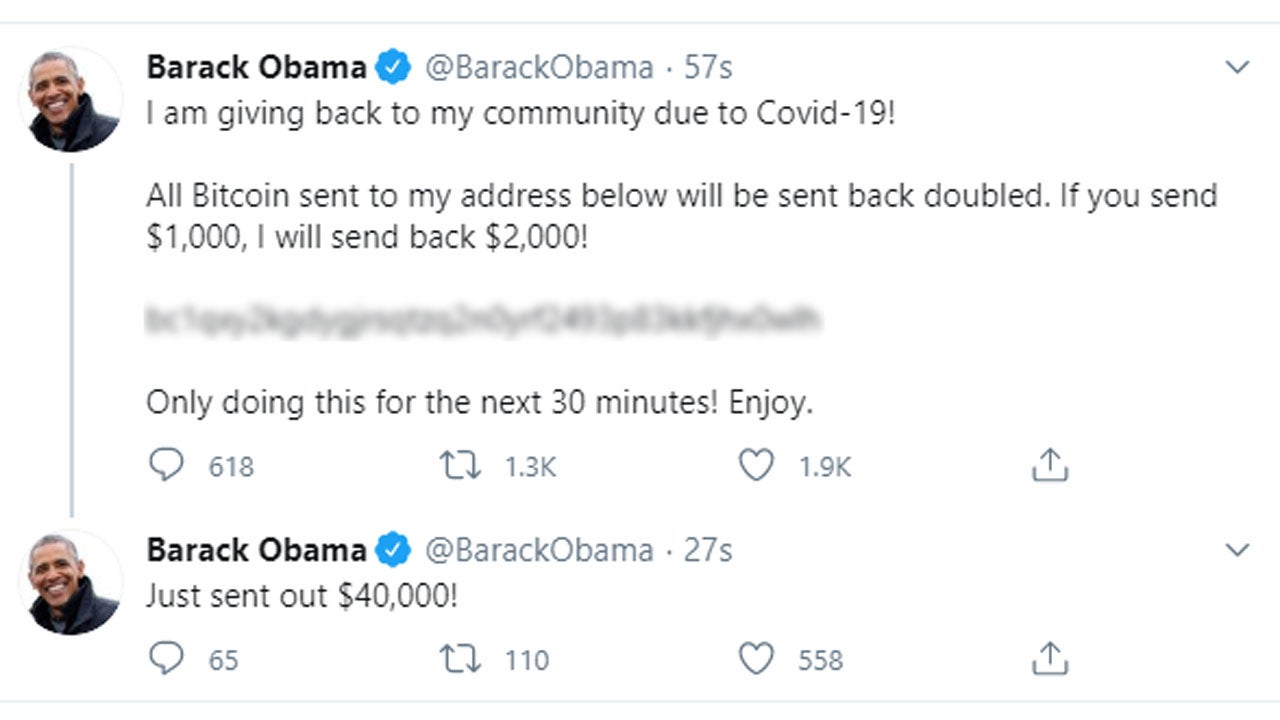
 TheTurbochargedSquirrel
> TheRealBicycleBuck
TheTurbochargedSquirrel
> TheRealBicycleBuck
07/17/2020 at 14:56 |
|
My company does this as phishing training. We all have a chrome extension that we use to flag these fake phishing emails (which also will flag real phishing emails for IT to handle). We click on one of the links in the fake emails and we have to retake the phishing training we all took during our onboardings.
 Kiltedpadre
> TheRealBicycleBuck
Kiltedpadre
> TheRealBicycleBuck
07/17/2020 at 15:00 |
|
My company’s security department will randomly send out suspect emails as a test to see how many people will report it to them as a phishing attempt. The percentage you catch then becomes one of the things they look at during your annual performance review. If you delete enough of the emails without reporting them first it can actually influence your next raise.
 jminer
> TheRealBicycleBuck
jminer
> TheRealBicycleBuck
07/17/2020 at 15:02 |
|
We do these a lot too - they’ve gotten much better to. I used to be able to just run a reverse DNS lookup on the name and it would route back to an internal IP making me laugh.
More recent ones have been timely like PTO expiration emails at the end of the year and so on.
Our place will even go as far as to fire you if you mess up enough of these after multiple trainings .
 TheRealBicycleBuck
> Kiltedpadre
TheRealBicycleBuck
> Kiltedpadre
07/17/2020 at 15:06 |
|
That’s an interesting twist. We don’t have a reporting requirement. Maybe if we did and it were tied to my next raise, I’d put more effort into reporting them.
At this point, I’m doing well just to read all of my email. A PM got mad at me this morning because I missed one of the 20 emails she sent me this week and it contained a request for information she needed yesterday.
Whoops.
 farscythe - makin da cawfee!
> TheRealBicycleBuck
farscythe - makin da cawfee!
> TheRealBicycleBuck
07/17/2020 at 15:10 |
|
our it guy just changes the passwords every couple months
then tapes the new password to the monitors on little laminated plaques
im thinking the dude has a pretty sweet gig going for himself...
welp...pointing out the security flaw is above my paygrade and im pretty sure the it guy knows.....sooo...its probably a management decision
 HammerheadFistpunch
> TheRealBicycleBuck
HammerheadFistpunch
> TheRealBicycleBuck
07/17/2020 at 15:14 |
|
We get those from time to time.
 user314
> TheRealBicycleBuck
user314
> TheRealBicycleBuck
07/17/2020 at 15:16 |
|
We get those periodically too. Once we got below a certain percentage of people actually clicking on the fake link s, management moved on to “Not clicking isn’t enough! W e want as close as possible to 100% reporting on phishing attempts!”.

 facw
> TheRealBicycleBuck
facw
> TheRealBicycleBuck
07/17/2020 at 15:33 |
|
Yeah, we get one from our IT security people every couple months. Plenty of people who should know better are fooled.
Side note, I hope you didn’t click the link in the email to get to the explanation. Will hurt your IT’s security numbers, and may get you signed up for some remedial training.
 ttyymmnn
> TheRealBicycleBuck
ttyymmnn
> TheRealBicycleBuck
07/17/2020 at 15:38 |
|
Invoicely?
Really?
 TheRealBicycleBuck
> facw
TheRealBicycleBuck
> facw
07/17/2020 at 15:50 |
|
Nope. I know better. I looked at the headers to figure out the originating domain.
 user314
> For Sweden
user314
> For Sweden
07/17/2020 at 16:01 |
|

 user314
> ttyymmnn
user314
> ttyymmnn
07/17/2020 at 16:05 |
|
Gotta be as realistic as possible.
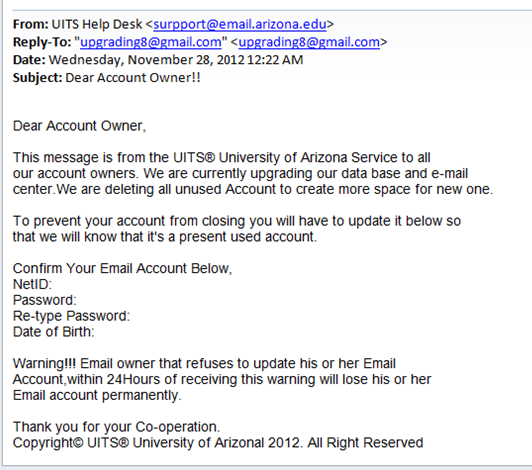
 ttyymmnn
> user314
ttyymmnn
> user314
07/17/2020 at 16:09 |
|
Seems legit. If it had been a real scam, they would have asked for your SSN.
 pip bip - choose Corrour
> TheRealBicycleBuck
pip bip - choose Corrour
> TheRealBicycleBuck
07/17/2020 at 19:51 |
|
sadly i have a co worker who isn’t that bright