 "shpuker" (shpuker)
"shpuker" (shpuker)
07/23/2015 at 20:15 ē Filed to: Hacking, Cherokee, Jeep, FCA, Chrysler, Hack, clusterfuck, CAN, Network, WiFi, wireless
 1
1
 18
18
 "shpuker" (shpuker)
"shpuker" (shpuker)
07/23/2015 at 20:15 ē Filed to: Hacking, Cherokee, Jeep, FCA, Chrysler, Hack, clusterfuck, CAN, Network, WiFi, wireless |  1 1
|  18 18 |

Recent hacks have sparked a renowned interest into the idea of automotive security and leaves the average consumer with a nearly universal question. ďWhat makes a car safe?!Ē Well Here goes nothing...
While perhaps the question more accurately on the mind of the average consumer is rather ďWhat car is safe and whereís the closest dealership?!Ē, I figure that this topic would turn into a pile of research into the control systems of varried manufacturers who, upon probing, would kindly tell me to fuck off. And that doesnít sound fun.
Disclaimer: Shpuker is an ďanonymousĒ (not that ^ anonymous) source on the internet that happens to be a student of mechanical/control systems engineering and thinks he has a respectable grasp on the concepts at play. He also pulled a play from DeMuroís playbook and wrote this all in the third person (and half drunk).
Before anything else itís important that you know how vehicles communicate between various controllers (computers). However Iíll attempt to dive as shallow as possible into the intricacies of vehicle communications for the sake of not boring you to death.
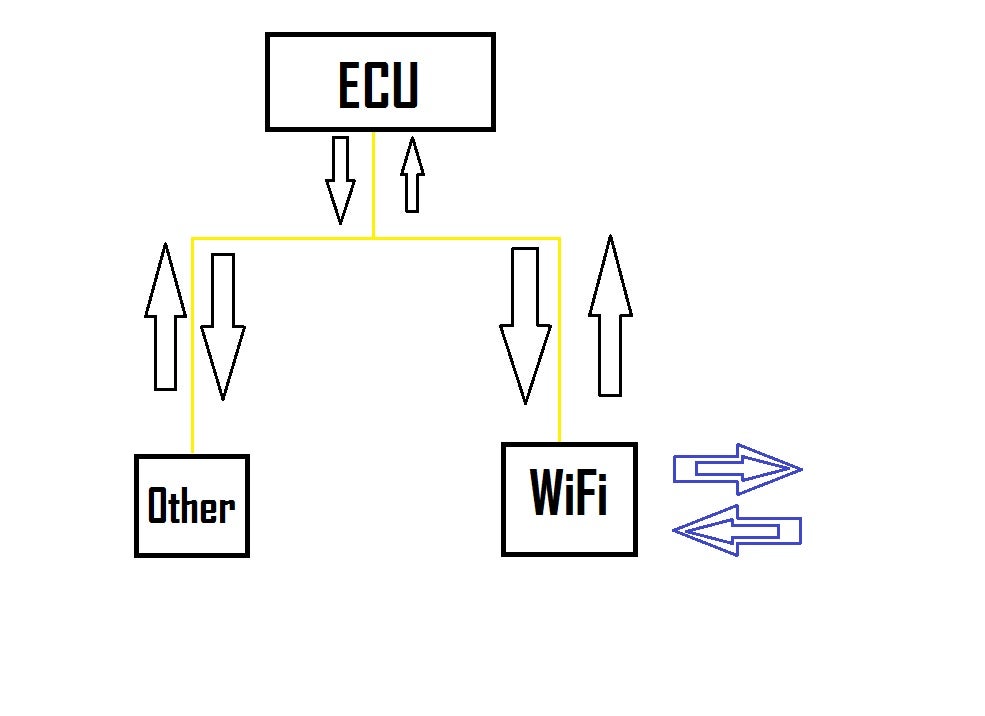
Currently automobiles communicate over an inter-controller communication network known as the Controller Area Network (CAN) which is essentially a system of wires that pass signals from one controller to one or many others (AKA itís a two way communication). This allows a vehicle to place sensors at one end of a vehicle and send them to one controller (that will typically control all of the resident functions in the area) which then talks back and forth with all other controllers connected to the same network by sending signals with different messages and priorities and if a controller gets two signals with the same message then it will pick the one with the higher priority and pass it on.
What are priorities and messages??
Well lets start with priorities. Each message sent over the CAN network has an identifier/priority associated with it, and once itís picked up by other controllers on the network it is then unpacked and gives certain parameters in the controller a specified value. Well then what could these messages possibly be then?! Messages contain these identifiers/priorities as well as a limited amount of other data.
This is neat and all but how does this impact automotive hacking?
Well Iím glad you asked! In short CAN communications on their own donít contribute much at all to the hacking of a vehicle. You didnít read that wrong, the CAN network on its own as a closed network is incredibly secure due to the fact that the only way into it is via physical connection. Where a network can become vulnerable rather lies in the nature of the components attached to it. Think of the security comparison like this:
A secured CAN network is like setting up a typewriter on your desk and knocking out a few pages while an unsecured network is more like hoping onto reddit at midnight on a Friday and clicking on everything in sight. (Bad analogy I know but close enough for this argument)
But what makes a network insecure?!
As with most things it requires a collection of circumstances to be true. First and foremost you have to think about whatís actually connected to the CAN network of your particular vehicle, but this isnít always easy to figure out. The biggest sign that something is likely transmitted over the CAN network is to look at any sort of adaptive controls on the system. For example ABS and traction control would both fall under this criteria.
Up to this point though the entire system is still based on physical connection, which leads us into our next circumstance, vehicles that transmit a wireless signal. Regardless of whether your vehicle is sending out a signal via OnStar, Bluetooth, of WiFi this puts it at a vastly elevated risk for hacking attacks in comparison to a fully wired vehicle. BUT THIS ALONE IS NO MEANS TO PANIC (yes that was necessary).
Well then when should I panic?
The Chrysler hack is a clear indicator that panic is quite the appropriate response to how modern vehicles set up with WiFi capabilities are configured. If this system were hard wired then they could only receive signals from the vehicle, and thus would present no risk for external attacks (essentially you canít shit on something that you arenít in the same continent as). Automakers are getting into trouble with their attempts to combine this capability with the ability to send simple signals to the vehicle over wireless signals however, and that is precisely what leaves a vehicle open to attack.
What makes the Cherokee so special?
Not much really. Jeep is by no means the only auto manufacturer offering a WiFi hotspot as a vehicle option and many other automakers even have remote access as a security benefit (think OnStar).
Warning, speculation ahead.
What I imagine Jeep failed to do was create a separation between the central CAN network of the vehicles but also a distinct failure to de-rate the priority of messages sent over wireless signal.
What this would create is a direct link over a simple WiFi connection to any system that is associated with the CAN network, typically including ABS, stability control, traction control, and on an increasing number of vehicles automated parking (all of which were compromised on the Cherokee and used to control the vehicle).
What can be done to separate these systems?
As an ideal solution, having a separate CAN network for non-essential communications only would effectively designate a low priority network capable of communicating the proper signals to each leg of the network without compromising essential parameters. I would imagine over the next few years however that a new standard for vehicle communication will begin to emerge with more priority and safety/encryption capabilities than current systems. Until then its up to manufacturers to put in an investment towards the security of their communications and to develop their products with these risks in mind.
 Mattbob
> shpuker
Mattbob
> shpuker
07/23/2015 at 09:10 |
|
there are possible security measures on CANbus as well. I know some systems use special security handshakes to get into specific modes where things can get dangerous. Simple checksums can also be helpful in this regard. I am really genuinely surprised that these systems on the cherokee were connected to the same CAN bus as the entertainment systems. Thats jsut being super cheap on Chryslers part. Frequently private buses are used for safety and engine control systems.
 You can tell a Finn but you can't tell him much
> shpuker
You can tell a Finn but you can't tell him much
> shpuker
07/23/2015 at 14:36 |
|
Why are entertainment and external communication systems hooked into the CAN system in the first place? Outside of laziness there is no reason that entertainment/bluetooth/wifi/cellular systems arenít air-gapped from the vehicle control systems.
 shpuker
> You can tell a Finn but you can't tell him much
shpuker
> You can tell a Finn but you can't tell him much
07/23/2015 at 20:02 |
|
My guess would be to make potential future features easier to implement. AKA say you want to add a feature that requires you to pull the tire pressure data from CAN that wasnít previously accounted for. Rather than having to go back and hard code the whole system to account for the change you can just pull that signal off CAN as well. As for why they made these communications physically capable of both read and write commands is a bit of a stretch. Iíd say they probably did it for the same reasons, however if you want a vehicle that can recieve wireless commands then you better damn well develop your own protocol with unique security measures.
 shpuker
> Mattbob
shpuker
> Mattbob
07/23/2015 at 20:07 |
|
I imagine they left the door open intentionally for some sort of future capability. Now that doesnít make it a good idea or even remotely ok but I imagine thatís their thought process. Then you get into the issue of why the hell they made their WiFi base read and write capable...
 AMGtech - now with more recalls!
> You can tell a Finn but you can't tell him much
AMGtech - now with more recalls!
> You can tell a Finn but you can't tell him much
07/24/2015 at 01:42 |
|
One reason is diagnostics, as entertainment systems become ever more complicated so do their problems. Itís a necessity these days to be able to communicate with almost every module, whether it be to read live data or install new software. There would have to be one ďcentral gatewayĒ where all networks merge.
What if you want to be able to see your vehicle speed displayed digitally in your instrument cluster, as well as your radio station and navigation directions? Wouldnít those different networks all HAVE to merge in the instrument cluster, or elsewhere, for that to happen?
 AMGtech - now with more recalls!
> shpuker
AMGtech - now with more recalls!
> shpuker
07/24/2015 at 01:57 |
|
Donít forget about:
-Flex-ray (CAN on steroids)
-MOST (media oriented system transport, fibre optics)
-LIN (local interconnect network, single wire master/slave setup)
All of these, including CAN, can be configured to operate at different speeds and capacities. Flex-ray is very fast and should have the highest priority because it is used almost entirely for safety systems. CAN is fast and comprises the vast majority of automotive communication with typical secondary priority, MOST operates at the speed of light but is only used for media and has low priority, LIN is typically used for very simple things like climate control actuators and alternators.
These are just general rules of thumb obviously, but having all of these definitely aids in security. Any manufacturer still using only CAN with Wi-Fi and Bluetooth is asking for a world of trouble. I mean come on, CAN has been around for about twenty years now!
Also see my reply to You can tell a Finn.
 AMGtech - now with more recalls!
> Mattbob
AMGtech - now with more recalls!
> Mattbob
07/24/2015 at 02:01 |
|
All of these things should definitely never be on the same network, however they shouldnít be completely separated from each other. There needs to be gateways between the dissent networks for various reasons. See my replies to You can tell a Finn and shpuker.
 BloodlessWeevil
> shpuker
BloodlessWeevil
> shpuker
07/24/2015 at 08:31 |
|
ďWhat I imagine Jeep failed to do was create a separation between the central CAN network of the vehicles but also a distinct failure to de-rate the priority of messages sent over wireless signal.Ē
No, it is setup exactly like that, just like every other modern car. Jeep does not have a monopoly on this problem.
 BloodlessWeevil
> You can tell a Finn but you can't tell him much
BloodlessWeevil
> You can tell a Finn but you can't tell him much
07/24/2015 at 08:36 |
|
Key-less entry, push button start, remote start, changing vehicle settings. All these things require the radio module to communicate with the rest of the vehicle. Maybe you would be willing to buy a car without those features, but the vast majority of buyers would not tolerate it.
 You can tell a Finn but you can't tell him much
> BloodlessWeevil
You can tell a Finn but you can't tell him much
> BloodlessWeevil
07/24/2015 at 09:33 |
|
You have completely missed the point of my comment. I never said those convenience and luxury items should be removed in the name of safety. I simply stated that entertainment systems and vehicle control systems should be air-gapped. That means that if someone were to remotely access the vehicle through a bluetooth/wifi/cellular signal there would be no connection from the entertainment system that they got into and the control systems that keep the vehicle safely on the road.
Quite simply there is no reason that the entertainment systems and any associated cellular/wifi/bluetooth/gps communication systems should be able to communicate and control safety critical systems on a vehicle. With proper safety and security protocols in place there is no reason that someone should be able to hack into my car through a cellular connection and control the engine, brakes or steering system remotely. There is no reason that things like keyless entry, push button starting or any other features would need to be sacrificed to maintain local control of safety critical systems.
 You can tell a Finn but you can't tell him much
> AMGtech - now with more recalls!
You can tell a Finn but you can't tell him much
> AMGtech - now with more recalls!
07/24/2015 at 09:49 |
|
Regarding diagnostics, most entertainment systems now come with USB, so there is a built in, nearly universal connector that can be used to read and write data to the entertainment systems. There is no reason that couldnít be used to perform diagnostics on entertainment system malfunctions without sending data to the OBD port through CAN. Sure, now youíve got to use two different connections to get the different systems, but Iíd be shocked if any shop level scan tool didnít already have a USB port included in it.
As for getting data to a secondary dash display, from a security perspective the best way would be to have a small screen that is simply a repeater wired in to the entertainment system and not connected to the CAN.
Beyond that, it just seems that it wouldnít be that unreasonable to put a firewall between the vehicle control systems and any external data sources. Iím not a computer security expert, so the difficulty of that isnít something that I can speak to. From a laymans perspective though there is no reason that someone outside the car should be able to control braking, throttle or steering.
 BloodlessWeevil
> You can tell a Finn but you can't tell him much
BloodlessWeevil
> You can tell a Finn but you can't tell him much
07/24/2015 at 10:08 |
|
No, I got it. Itís just that those functions use wifi protocols (unlike earlier key-less entry systems.) Separating the transceiver for those functions from the one for entertainment functions does not buy you much from a security standpoint.
 AMGtech - now with more recalls!
> You can tell a Finn but you can't tell him much
AMGtech - now with more recalls!
> You can tell a Finn but you can't tell him much
07/24/2015 at 10:08 |
|
Good points for sure. The USB idea is already somewhat in use, at least on some of the latest Mercedes for programming. And I like the secondary display idea.
But utilizing different types of networks (see my response to shpuker) builds in some security. As far as I know (Iím no programmer) Mercedes at least writes their software so that things like navigation etc. have no authority to tell any critical system what to do.
I would be interested to sit in on a conversation where they decide how all of this stuff is going to be laid out and programmed.
 shpuker
> AMGtech - now with more recalls!
shpuker
> AMGtech - now with more recalls!
07/24/2015 at 19:20 |
|
My moneyís on fiber taking the lead role within a few years. Itís an improvement on literally every flaw of the current CAN networks (aside from cost). Speed is un-real, security is boundless, message length/detail is incredible, etc.
 shpuker
> BloodlessWeevil
shpuker
> BloodlessWeevil
07/24/2015 at 19:21 |
|
Iím not saying theyíre the only ones that have made, or will make, this mistake. Iím saying they shouldíve known better.
 shpuker
> You can tell a Finn but you can't tell him much
shpuker
> You can tell a Finn but you can't tell him much
07/24/2015 at 19:25 |
|
Iím at a loss as to why they didnít. At the very least I would expect them to use hardware restrictions in order to keep the WiFi base from writing into the CAN. I imagine some engineer along the way left the door open on purpose for some imagined future capability? IDK Iím stretching a bit now.
 AMGtech - now with more recalls!
> shpuker
AMGtech - now with more recalls!
> shpuker
07/24/2015 at 22:57 |
|
Definite possibility. But flex-ray is also a huge improvement over CAN and seems to be the direction theyíre headed for the moment. But moments are fleeting.
 shpuker
> AMGtech - now with more recalls!
shpuker
> AMGtech - now with more recalls!
07/25/2015 at 00:42 |
|
All too true. At least from the industrial side of CAN use I can say the majority of people that Iíve talked to or worked with are waiting for a new automotive standard before making any moves and that ideal seems to aim towards fiber. However the market is inherently hard to predict so who knows, maybe weíll be introduced to some new inter-network communication style that makes everything else obsolete before then.